44 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
4.6.6 Flashcards - Quizlet Which of the following is a form of attack that tricks victims into providing confidential information, such as identity information or logon credentials, ... 3.5 Flashcards | Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. 1) An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/or requires that access. Masquerading
CompTIA Network Certification Exam N10-007 Questions and Answers A. Reverse the wires leading to pins 1 and 2. B. Reverse the wires leading to pins 1 and 3. C. Reverse the wires leading to pins 2 and 3. D. Reverse the wires leading to pins 2 and 4. 3. An office network consists of one two-port router connected to a 12-port switch. A four-port hub is also connected to the switch.
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
CyberSecurity Chapter 3 Flashcards | Quizlet You have recently discovered that a network attack has compromised your database server. Te attacker may have stolen customer credit card numbers. You have stopped the attack and implemented security measures to prevent the same incident from occurring in the future. What else might you be legally required to do Joints and Skeletal Movement | Boundless Biology - Course Hero The point at which two or more bones meet is called a joint or articulation. Joints are responsible for movement (e.g., the movement of limbs) and stability (e.g.,the stability found in the bones of the skull). There are two ways to classify joints: on the basis of their structure or on the basis of their function. What are the 12 cranial nerves? Functions and diagram The optic nerve transmits information to the brain regarding a person's vision. When light enters the eye, it hits the retina, which contains rods and cones. These are photoreceptors that translate...
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.. Security Pro Chapter 2 - 2.1.6, 2.2.4, 2.3.4, 2.4.3, 2.5 ... - Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. ○ Vishing ○ Piggybacking Test 1 Flashcards - Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. ○ Vishing ○ Piggybacking 5.8.3 Practice Questions Flashcards - Quizlet Drag the network attack technique on the left to the appropriate description or example ... (Each technique may be used once, more than once, or not at all.). 4 Heart Valves: What They Are and How They Work - Cleveland Clinic As your heart pumps blood, four valves open and close to make sure blood flows in the correct direction. As they open and close, they make two sounds that create the sound of a heartbeat. The four valves are the aortic valve, mitral valve, pulmonary valve and tricuspid valve. A heart murmur is often the first sign of a heart valve problem.
Dystonias Fact Sheet | National Institute of Neurological Disorders and ... Idiopathic dystonia refers to dystonia that does not have a clear cause. Many instances of dystonia are idiopathic. There are several genetic causes of dystonia. Symptoms may vary widely in type and severity even among members of the same family. In some instances, people who inherit the defective gene may not develop dystonia. Spear phishing an attacker gathers personal - Course Hero Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Not all terms are used . An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/orrequires that access. Masquerading 32 UI Elements Designers Need To Know - CareerFoundry You'll commonly find the hamburger menu on the top left-hand corner of apps and most likely containing a group of navigation links. 14. Icon Icons are images used to communicate a variety of things to users. They can help to better communicate content, or can communicate and trigger a specific action. Security Plus 601 Flashcards - Quizlet O A server back door allows an attacker on the internet to gain access to the intranet site. O A water pipe in the server room breaks. O A delivery man is able to walk into a controlled area and steal a laptop. O A user accidentally deletes the new product designs. A user accidentally deletes the new product design
Instruction: Drag the tiles to the boxes to form correct pairs. Not all ... Instruction: Drag the tiles to the boxes to form correct pairs. Not all tiles will be used. Match each pair of points A and B to point C such that the measure of Angle ABC=90*. Tiles 1. A (3, 3) and B (12, 6) 2. C (6, 52) 3. A (-10, 5) and B (12, 16) 4. C (16, -6) 5. A (-8, 3) and B (12, 8) 6. C (18, 4) 7. A (12, -14) and B (-16, 21) 8. C (-11, 25) Brainly.com - For students. By students. The Brainly community is constantly buzzing with the excitement of endless collaboration, proving that learning is more fun — and more effective — when we put our heads together. Help the community by sharing what you know. Answering questions also helps you learn! Shoneitszeliapink. Biology. Classical Conditioning: How It Works With Examples Classical conditioning involves forming an association between two stimuli, resulting in a learned response. 4 There are three basic phases of this process. Phase 1: Before Conditioning The first part of the classical conditioning process requires a naturally occurring stimulus that will automatically elicit a response. The immune system review (article) | Khan Academy The immune system responds to antigens by producing cells that directly attack the pathogen, or by producing special proteins called antibodies. Antibodies attach to an antigen and attract cells that will engulf and destroy the pathogen. The main cells of the immune system are lymphocytes known as B cells and T cells.
Threats, Attacks, and Vulnerabilities Flashcards | Quizlet A wormworm is a self-replicating program that uses the network to replicate itself to other systems. A worm does not require a host system to replicate. Both viruses and worms can cause damage to data and systems, and both spread from system to system, although a worm can spread itself while a virus attaches itself to a host for distribution
Test Out 3 - Subjecto.com Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Vishing Piggybacking Spam Phishing Whaling Spear phishing Masquerading Spim Tailgating.
A&P 2, Unit 2, Chapter 22 Homework Flashcards - Quizlet Not all terms will be used., Select the correct word from the list to complete ... Drag each label into the appropriate position to identify what type of ...
Security Pro Midterm Review 1-4 Flashcards - Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. ○ Vishing ○ Piggybacking
How to Deal With Social Media Defamation & Libel - Minc Law Social media defamation is an all-encompassing term used to describe a false statement of fact about a third party published to a social media website, platform, or app, such as Facebook, Twitter, or Instagram. Social media defamation is often referred to as 'social media slander' or 'slander on social media.'
ReaderUi ReaderUi
Test Out 1-4 Flashcards - Quizlet Perform additional investigations to identify the attacker Contact your customers to let them know about the security breach Delete personally identifiable information from your computers Contact your customers to let them know about the security breach THIS SET IS OFTEN IN FOLDERS WITH...
Romanesque Architecture | Boundless Art History - Course Hero The Cistercians are a Roman Catholic religious order of enclosed monks and nuns. This order was founded by a group of Benedictine monks from the Molesme monastery in 1098, with the goal of more closely following the Rule of Saint Benedict. Characteristics of Cistercian Architecture
What Are Leukocytes? - Definition, Types & Function - Study.com Leukocytes -- a body's army of soldiers -- are a part of our immune system. They not only fight the germs that cause disease and infections, they strive to protect us against any foreign agent ...
White Blood Cells | Boundless Anatomy and Physiology - Course Hero White blood cells (WBCs), or leukocytes, are immune system cells that defend the body against infectious disease and foreign materials. There are several different types of WBCs. They share commonalities but are distinct in form and function. WBCs are produced in the bone marrow by hemopoeitic stem cells, which differentiate into either ...
Exam az-900 - All Questions | Exam-Answer Fault tolerance is the ability of a system to continue to function in the event of a failure of some of its components. In this question, you could have servers that are replicated across datacenters. Availability zones expand the level of control you have to maintain the availability of the applications and data on your VMs.
Levels of Measurement: Nominal, Ordinal, Interval and Ratio There are actually four different data measurement scales that are used to categorize different types of data: 1. Nominal. 2. Ordinal. 3. Interval. 4. Ratio. In this post, we define each measurement scale and provide examples of variables that can be used with each scale. Nominal. The simplest measurement scale we can use to label variables is ...
Test out 3.5 and 3.6 Flashcards - Quizlet Vishing. An attacker uses a telephone to convince target individuals to reveal their credit card information. Which of the following is a common social ...
physiology 1 Flashcards - Flashcard Machine - Create, Study and Share ... D) There is no force on either ion to move. E) Forces on both sodium and potassium ions are to move into the cell. Definition. B) The force on sodium ions is to move into the cell, and the force on potassium ions is to move out of the cell. Term. Given a cation with an equilibrium potential of -55 mV.
Chapter 8-Protecting Your System: User Access Security, from ... The following countermeasures address user access security concerns that could affect your site (s) and equipment. These strategies are recommended when risk assessment identifies or confirms the need to counter potential user access breaches in your security system. Countermeasures come in a variety of sizes, shapes, and levels of complexity.
What are the 12 cranial nerves? Functions and diagram The optic nerve transmits information to the brain regarding a person's vision. When light enters the eye, it hits the retina, which contains rods and cones. These are photoreceptors that translate...
Joints and Skeletal Movement | Boundless Biology - Course Hero The point at which two or more bones meet is called a joint or articulation. Joints are responsible for movement (e.g., the movement of limbs) and stability (e.g.,the stability found in the bones of the skull). There are two ways to classify joints: on the basis of their structure or on the basis of their function.
CyberSecurity Chapter 3 Flashcards | Quizlet You have recently discovered that a network attack has compromised your database server. Te attacker may have stolen customer credit card numbers. You have stopped the attack and implemented security measures to prevent the same incident from occurring in the future. What else might you be legally required to do



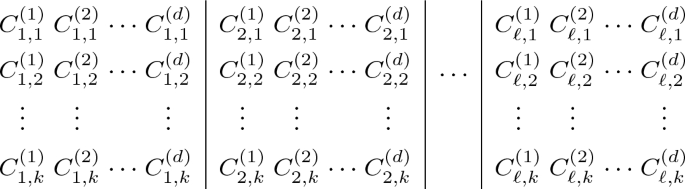
















Post a Comment for "44 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used."